
Data is key in driving the usage of any SaaS (Software as a Service)-based application. Data also ensures that there are no gaps in terms of usage experience. Every user/employee wants a seamless process when they use any mobile or web application. Pre-loaded data ensures that the application works smoothly. Businesses share critical financial information with partner vendors who set up applications to help improve the ‘ease of doing business’ quotient. Therefore, the importance of data security in travel & expense cannot be overstated.
The business travel & expense industry is now shifting to a software backed landscape. Hence, it’s of utmost priority to strategize how we can protect the data from any external attack or contingency.
What is Data Security?
Data is the basic building block of an organization just like employees, infrastructure etc. Any organization’s most valuable asset is its users’ data and records. In simple words, the meaning of data security is the protection of an organization’s data against unauthorized access or modification in order to maintain its integrity, confidentiality, and availability.
- Integrity – trust that the data is correct and has not been manipulated or shared
- Confidentiality – only authorized users have access to it
- Availability – making sure that the data is accessible whenever required
What Data Security Means in Travel & Expense
Travel & Expense companies generally require two types of data inputs to ensure a smooth travel booking and expense filing process.
- PII Data – Every employee’s Personal Identifiable Information (PII) serves as a key input to Travel & Expense management. The following data inputs serve as personal identifiers in a T&E setup.
- Name
- Date of birth
- Gender
- Email ID
- Phone number
- Designation
- Passport details
- Credit card details
Other information such as frequent flyer number, although neither a mandatory input nor a personal identifier, could still be added to make a user’s travel booking and expense filing journey convenient.
- Company data – In order to get the best out of their T&E platforms, businesses can choose to integrate their acquired T&E platform with the Human Resource Management Systems (HRMS) and/or their Accounting/ERP software. This is done so that there is an easy flow of data (employee details, business expenses, travel data) between the travel & expense platform and the HRMS/ERP/Accounting software. Companies also sometimes add their corporate credit cards for seamless monthly subscription payments.
All of this data flows seamlessly between multiple systems, as shown below, in order to provide a fully integrated travel & expense management platform to you.
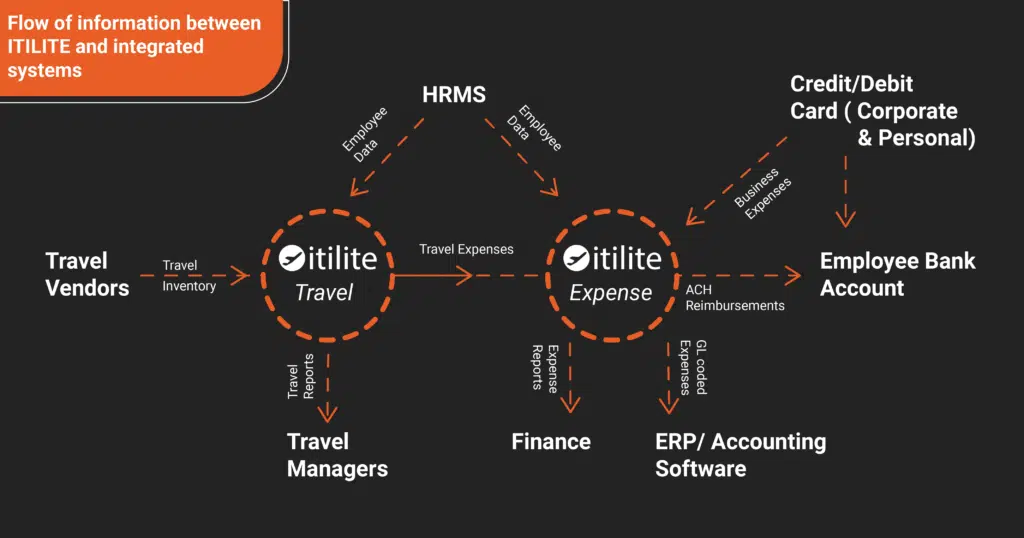
How ITILITE Sets the Foundation to Protect the Data Provided by our Customers
Ensuring the security of both the Employee PII data and the company data should be one of the key mandates for any Travel & Expense company. At ITILITE, we make it our top priority to protect the data and information that our 300+ clientele has entrusted us with.
We provide end-to-end encryption on all their information, especially banking and credit card data. In addition to this, ITILITE also takes care of server configuration, patching, logging infrastructure, incident detection, and response. These are some of the services which companies have to otherwise employ their internal teams to manage. Chief Trust Officers at several companies in the past have listed this as one of the ancillary benefits of being associated with ITILITE.
Dedicated Teams for Data Security
When we first started out in our journey to gather our customer data, one of the ruling directives of the founders was to establish a dedicated ISMS (Information Security Management System) Team that sets direction, policy, analysing and advisory on how to manage data security risks along with user access management. This team is also in-charge of information security awareness & training for the rest of the organization.
The leadership team at the company has also formed another committee called ERMC (Enterprise Risk Management Committee). This team reviews security incidents, reviews and approves data security objectives and checks effectiveness of security implementation of controls.
The onboarding program for developers at ITILITE includes training in secure coding. They have been trained on Open Web Application Security Project® (OWASP), Common Vulnerabilities and Exposures (CVE) and mitigation methodologies. This ensures stringent security protocols on our Secure Software Development Life Cycle (SSDLC). Follow-up sessions are also done to make sure they are at the top of their game on any given day.
Our Quality Assurance (QA) team does timely checks on suitability, performance and stability before the features are released. Best practices for data security and for ensuring data privacy are embedded in every feature release cycle.
How we have Built Multiple Levels of Protection
Physical Access Control and Security –
- We have a strong physical control system in place, with visitors to the premises entering only through an access control system. This is monitored 24 hours a day, seven days a week by CCTV.
- The Server room access is limited to required individuals only and the room is controlled by the Building Monitoring System.
Incident Monitoring –
An incident could be anything. For example – Multiple failed login attempts or multiple attempts on credit card pin inputs. ITILITE follows a thorough incident monitoring process that includes log monitoring, file monitoring, security groups, configurations, audit trails etc.
- We generate system logs, audit logs and back them up regularly so as to analyze audit trails when required.
- We use SIEM (Security Information and Event Management) tools to detect incidents in our ecosystem in real-time.
Vendor Management –
While onboarding any vendor that helps us provide a more convenient user experience, each vendor’s data security practices are evaluated. Also, contractual measures are used to ensure that all data security practices are followed. The performance of every vendor is evaluated annually.
Availability and Redundancy –
- There are set business continuity plans in place in case of emergencies. This ensures there is no loss of client information and the platform is available for all client needs 24×7. Periodic backups are taken so as to be well-prepared for any calamity.
- Near real-time backups are taken across multiple availability zones in encrypted and access-controlled containers.
Why you should Place your Trust in us
Highest Levels of Governance, Regulatory and Compliance in the Industry
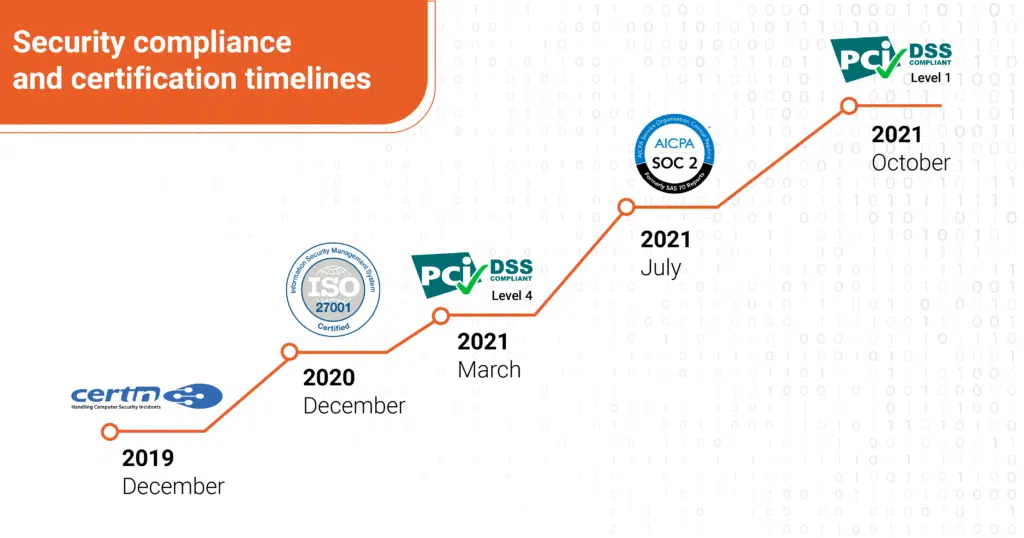
We strive to continually enhance the security, the technicality, and the organizational measures that protect sensitive information shared with us. Our comprehensive security programs are dedicated to all aspects of security. With the highest regard to industry compliance, we hold trusted security certifications. Some of the top-drawer security certifications we can boast about are:
- CERT-IN certification for Application Security – We deploy security protocols to identify, repair, and protect our application against security weaknesses throughout the application life cycle
- ISO 27001:2013 – Globally renowned standard which helps to establish, implement, operate, monitor, review, maintain and continually improve an ISMS
- SOC2 – Allows to securely manage data and help protect the interests of our organization and the privacy of our clients
- GDPR certification – The way we collect and process data provided by our customers is compliant to the General Data Protection Regulation (GDPR) set by the European Union
- Level 1 PCI DSS Compliance – Level 1 is the most stringent of the compliance levels for protecting customer card data
End-to-End Encryption –
Our client’s data is stored with AES 256-bit encryption with 1,024-bit key-strength for data at Rest and FIPS 140-2 compliant TLS v 1.2 encryption for data in transit. AES algorithms are almost impossible to crack, with longer key lengths offering additional protection. TLS algorithms ensure data retains its integrity during transition and helps provide confidentiality through encryption.
Additionally, Role-based access through an explicit need-to-know basis policy and two-factor authentication (2FA) is available. This ensures that the client data is secured and is accessible only to a select group of people.
Robust Product Structure –
Our highly resilient product architecture with n+1 component redundancy, and periodic backups keeps us ready for all sorts of calamities be it man-made or natural. The best proof of that was during the Covid-19 pandemic, when our product not only sustained but thrived and delivered seamless services to our clients.
Best-in Class Security for all your Travel & Expense Data
ITILITE is the safest haven for travel & expense management. The ISMS and ERMC teams work day and night to ensure all safety protocols are followed to the dot. With the highest compliance levels of compliance in the industry for security of application data, credit cards and employee personal data coupled with a multi-level approach to protection, your travel & expense data cannot be in safer hands.
Get ITILITE today by requesting for a demo below and automate your travel & expense management processes, while keeping all your data fool-proof.













